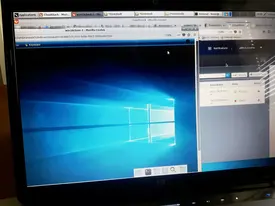
Linux-based Active Directory management
Linux-based Active Directory management
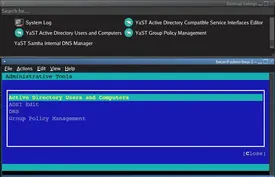
Upcoming article. Delayed.
Managing & controlling Windows client computers is possible not only with a Windows Active Directory domain controller but also with a Linux-based Active Directory domain controller. However, is the setup viable in real life scenarios? There are multiple factors which should be taken into account when considering a non-standard Active Directory approach. To seek the answer, multiple data analysis methods and various Active Directory scenarios in a simulated network topology are used.
The article is based on my Business Information Technology thesis work.
 Enforced, encrypted, self-hosted DNS solution for Android devices
Enforced, encrypted, self-hosted DNS solution for Android devices
 Kerberos-secured network file shares - practical guide for kerberized NFSv4
Kerberos-secured network file shares - practical guide for kerberized NFSv4

 HikinGrounds: A website for outdoor people
HikinGrounds: A website for outdoor people
 OpenNTPD - now with OpenSSL support
OpenNTPD - now with OpenSSL support
 USB authentication for Linux computers and users
USB authentication for Linux computers and users
 Run Android apps on Linux desktop with LXC
Run Android apps on Linux desktop with LXC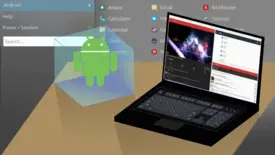

 SQL database planning, development & usage
SQL database planning, development & usage
 Fighting dotfile pollution on Linux
Fighting dotfile pollution on Linux


 Automating Windows Active Directory deployment
Automating Windows Active Directory deployment



 Adventures in cloud
Adventures in cloud